Cite this problem as Problem 24.
Problem
Can all bipartite entangled states be used to generate secret keys?
Background
Given three parties Alice, Bob, and Eve, initially holding quantum systems ![]() a local operation on Alice’s side is a quantum channel
a local operation on Alice’s side is a quantum channel ![]() , i.e. a completely positive trace preserving map
, i.e. a completely positive trace preserving map ![]() . Analogously, one can define a local operation on Bob’s side. A public communication step is the process of transmitting a classical register from Alice to Bob and Eve, or from Bob to Alice and Eve. This can be modelled by the state-to-state transformation
. Analogously, one can define a local operation on Bob’s side. A public communication step is the process of transmitting a classical register from Alice to Bob and Eve, or from Bob to Alice and Eve. This can be modelled by the state-to-state transformation
![]()
where ![]() are registers held by Alice, Bob, and Eve, respectively. In other words, Eve, who represents the eavesdropper, can always overhear what Alice is communicating to Bob, or vice versa.
are registers held by Alice, Bob, and Eve, respectively. In other words, Eve, who represents the eavesdropper, can always overhear what Alice is communicating to Bob, or vice versa.
Secret key is distilled from quantum states by carrying out (finitely many) rounds of local operations and public communication. The resulting procedures are usually called LOPC protocols. We will write ![]() when we want to stress which systems at the input/output belong to Alice, Bob, and Eve.
when we want to stress which systems at the input/output belong to Alice, Bob, and Eve.
Given a very large number ![]() of copies of some tripartite state
of copies of some tripartite state ![]() , we can ask how much secret key Alice and Bob can generate out of it using LOPC protocols only. Specifically, they will apply an operation
, we can ask how much secret key Alice and Bob can generate out of it using LOPC protocols only. Specifically, they will apply an operation ![]() to the initial state
to the initial state ![]() , where
, where ![]() denotes the system made of
denotes the system made of ![]() copies of
copies of ![]() , and analogously for
, and analogously for ![]() . The aim, at the end of the protocol, is to have Alice and Bob share a perfect secret key on some classical registers
. The aim, at the end of the protocol, is to have Alice and Bob share a perfect secret key on some classical registers ![]() and
and ![]() made of
made of ![]() bits each (square brackets indicate the integer part). Here,
bits each (square brackets indicate the integer part). Here, ![]() represents the rate of key generation. In order for the protocol to be deemed successful, the final state should be
represents the rate of key generation. In order for the protocol to be deemed successful, the final state should be
![Rendered by QuickLaTeX.com \displaystyle \Lambda_n\big(\rho_{ABE}^{\otimes n}\big) \approx \left(2^{-[Rn]} \sum_{x=0}^{2^{[Rn]}-1} |x\rangle\!\langle x|_{K_n} \otimes |x\rangle\!\langle x|_{K'_n}\right) \otimes \sigma_{E'_n}\, ;](https://oqp.iqoqi.oeaw.ac.at/wp-content/ql-cache/quicklatex.com-80fc904dae6aac63c46819cf69e778ae_l3.png)
that is, Alice and Bob should hold ![]() perfectly correlated bits, constituting their secret key, while Eve should only hold a state that is uncorrelated with Alice’s and Bob’s keys.
perfectly correlated bits, constituting their secret key, while Eve should only hold a state that is uncorrelated with Alice’s and Bob’s keys.
Partial Results
- In [1] it is shown that some bound entangled states do allow the extraction of a secret key. This is an extreme counterexample to the idea that secret key is best generated from an entangled state by first distilling pure singlets, and using these to get the key. In principle, this provides a new distinction among bipartite states in those which allow key generation and those which do not. The problem asks whether this is really a new distinction.
- [2] provides a one-way distillation protocol being able to distill secret key and EPR-Pairs.
- In [3] a class of bound entangled states with positive key rates is provided. The smallest state of this kind is
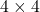 , which shows that peculiar security contained in bound entangled states does not need high dimensional systems. For distilling key the Devatak-Winter protocol [2] is used.
, which shows that peculiar security contained in bound entangled states does not need high dimensional systems. For distilling key the Devatak-Winter protocol [2] is used. - In [4] a protocol is presented which enables two parties to extract from untrusted states an arbitrarily long and secure key, even though the amount of distillable entanglement of the untrusted states can be arbitrarily small.
References
[1] K. Horodecki, M. Horodecki, P. Horodecki, and J. Oppenheim, Secure key from bound entanglement, Phys. Rev. Lett. 94, 160502 (2005) and arXiv:quant-ph/0309110 (2003).
[2] I. Devetak and A. Winter, Distillation of secret key and entanglement from quantum states, Proc. R. Soc. Lond. A 461, 207-235 (2005) and arXiv:quant-ph/0306078 (2003).
[3] K. Horodecki, L. Pankowski, M. Horodecki, P. Horodecki, Low-dimensional bound entanglement with one-way distillable cryptographic key, IEEE Trans. Inf. Theory 54, 2621 (2008) and arXiv:quant-ph/0506203 (2005).
[4] K. Horodecki, D. Leung, H.-K. Lo, and J. Oppenheim, Quantum key distribution based on arbitrarily weak distillable entangled states, Phys. Rev. Lett. 96, 070501 (2006) and arXiv:quant-ph/0510067 (2005).